 Early in July, IBM announced that they have developed an ultra-dense computer chip that has roughly four times the computing capacity of today’s most powerful chips. These prototype chips, and ones they will develop to fuel computing into the next decade and beyond, are the result of the evolution of 21st century informatics.
Early in July, IBM announced that they have developed an ultra-dense computer chip that has roughly four times the computing capacity of today’s most powerful chips. These prototype chips, and ones they will develop to fuel computing into the next decade and beyond, are the result of the evolution of 21st century informatics.
Moore’s Law is an observation made in a 1965 paper by the co-founder of Intel, Gordon Moore. Moore’s Law suggests the number of transistors per square inch on integrated circuits will double every year since they were invented and would continue to do so. This theory has seen some difficulty entering its fifth decade. That’s not to say that this “law,” that has held up well for decades, has been proven false, but eventually, it will inevitably fail. In an interview for Time magazine, renowned theoretical physicist Michio Kaku said:
...we will see the collapse of Moore’s Law. In fact, already, we see a slowing down of Moore’s Law. Computer power simply cannot maintain its rapid exponential rise using standard silicon technology. Intel Corporation has admitted this.
To counteract this prediction, the scientists at IBM, Intel, AMG and other research facilities, have begun using alternative materials to produce a density that allows for billions of transistors to be built into a single chip. This presents a challenge for these manufacturers to consistently produce chips that pushes computing capabilities forward. IBM’s new chips are made from a silicon-germanium alloy that produces the necessary semiconducting material needed to successfully produce integrated circuits for transistors.
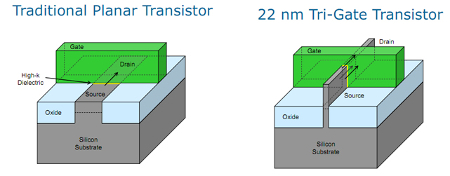
Currently, the most advanced commercially available chip, Intel’s i7-5960X processor has 2.6 billion transistors, and is built with a 22-nanometer process with their Tri-Gate 3D design. IBM’s newest chips have 20 million transistors and are built with a 7-nanometer process. To put that in perspective, the width of a human hair is between 80,000 and 100,000 nanometers. This comparison explains how these manufacturers are producing so many transistors in such a small space, as the average computer chip is the size of a postage stamp.
As computing systems have become more predominant in the 21st century, the progress of computing, and the sustained viability of Moore’s Law, relies on these nano technicians’ ability to find materials that will facilitate tens of billions of transistors. As of now, they have been able to do so, but eventually, we may need to look elsewhere to get more from our technology.
Do you think this technology will be developed to sustain Moore’s Law into the next decade, or will it fail? Share your thoughts in the comments below.


