 The hype is still strong for Windows 10, and it’s easy to see why. It’s a great operating system that has the potential to change the way your business performs its daily duties. However, the monthly desktop operating system usage statistics released by NetMarketShare hint that Windows 10 adoption is starting to slow down and that many users are simply opting to keep using Windows 7, Windows 8, and Windows 8.1. What gives?
The hype is still strong for Windows 10, and it’s easy to see why. It’s a great operating system that has the potential to change the way your business performs its daily duties. However, the monthly desktop operating system usage statistics released by NetMarketShare hint that Windows 10 adoption is starting to slow down and that many users are simply opting to keep using Windows 7, Windows 8, and Windows 8.1. What gives?
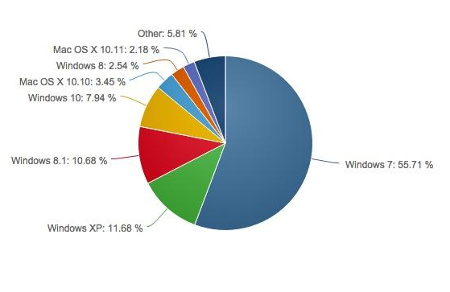
As of October 2015, only 7.84 percent of desktop users are taking advantage of Windows 10, while Windows 7 retains its predominant percentage on 55.71 percent of desktops. Windows 8 and 8.1 combined make up about 13.22 percent. What’s most concerning about this chart is that Windows XP, a completely unsupported operating system that’s considered a hindrance and a threat to any business currently using it, still accounts for 11.68 percent of all desktops.
Despite the fact that Windows 10 is a great new operating system, there are plenty of folks out there who still retain the viewpoint that “if it’s not broken, don’t fix it.” The primary problem with this view of technology is that people often forget that it might not be broken now, but soon enough it most certainly will be. As we’ve seen from Windows XP, people will continue to use an unsupported operating system well past its expiration date for the sole purpose that they’re used to it and feel that there’s very little risk in doing so. Little do they know, however, that continuing to use unsupported systems can have unexpected side-effects.
In a way, using expired technology is like continuing to use milk past its expiration date. Sure, it might be okay for a day or two past the “sell by” date, but sooner or later, you’re going to pour a glass of milk and reel back in disgust. Then you’ll be out of luck for any recipes that require milk until you buckle down and purchase some new milk. Similarly, your technology might seem fine past its expiration date, but running unsupported software will leave your systems wide open to attacks from threats specifically designed to infiltrate your expired systems. This means that it’s your responsibility to take proactive measures and “buy some new milk” before your technology expires completely. All it takes is a single flaw to allow hackers into your system’s network; hackers aren’t picky with how they infiltrate your network, and failing to use a supported piece of software or operating system is a great way to give cyber threats a head start.
Voyage Technology’s qualified technology professionals have the skills necessary to deploy patches and security updates for all of your mission-critical systems so that the responsibility of doing so doesn’t rest on your business’s shoulders. We can remotely monitor and maintain your systems whenever regular maintenances are needed. This means that you don’t have to worry about performing the maintenance yourself, and you can continue improving your business with the peace of mind necessary to achieve great things.
Furthermore, updating your workstation operating systems can be difficult, especially if you use legacy applications that may not be functional with more recent operating systems. In cases like this, it’s best to have a technology professional on standby (like those at Voyage Technology) whom you can consult. This helps to make sure that you aren’t taking too many risks by upgrading to a more recent operating system.
Despite Windows 10’s slow growth, your business can drastically improve operations by giving it a chance. To discuss how adopting Windows 10 can affect your business’s operations, give us a call at 800.618.9844.


