Making IT decisions while balancing the user experience—including their complaints—can be exhausting. As a decision maker for your business, you have a budget to consider, as well as a timeline to manage. You’ll have to say no, which no one likes to hear, but it’s a necessary part of running your organization effectively.
Voyage Technology Blog
Remote work has changed the way that businesses approach normal operations. Due in large part to the disruptions of the past couple of years, remote work has become a staple of the business environment, and while you might hear stories of businesses pushing hard to return to the workplace, the reality is that they are the exception rather than the norm.
You and your employees are likely exhausted from dealing with technology day in and day out. Even if it is what allows businesses to flourish, you still might want some time away from it from time to time. When it feels like too much, know that a digital detox can be a valid way of temporarily moving away from technology—even in the workplace.
While sitting all day might sound appealing at first glance (after all, who doesn’t like sitting?), it’s not something that our bodies are designed to do. Sitting, as a result, can have considerable negative consequences on our overall health when done in excess. It doesn’t have to be hard to fit a workout into your day, though; you can do these simple desk-ercises right from your office to combat the creep of becoming too sedentary.
Cybersecurity is complicated, with countless moving parts that all contribute to a well-protected network. This includes password changes, multi-factor authentication, and policies and procedures that could make the average workday a headache for the average office worker. Cybersecurity burnout is a real thing, and it’s becoming a major problem for businesses that don’t approach it intentionally.
All companies have policies in place which govern how their employees use their technology, so it makes sense that any new employees should be onboarded in accordance with these expectations. Let’s go over how you can make sure your new employees know and understand your organization’s policies as they relate to business technology.
Back during the holiday season, the Federal Trade Commission shared some data that showed that members of Generation X, Millennials, and Generation Z are all more likely to fall for online shopping scams than those over the age of 60…and not by a little, either. Those under that age are apparently 86 percent more likely to fall for these scams.
Technology is a major player in today’s business environment, and in most cases, companies have someone in their executive suite whose sole purpose is overseeing their technology systems. This individual—the Chief Information Officer, or CIO—is incredibly important to the everyday operations of businesses.
We know it’s not pleasant to think about your organization succumbing to a cybersecurity attack, but it’s a very realistic event that you have to be prepared for. Let’s take a look at the statistics and how exactly they are not in your business’ favor.
Remote work might have been crucial in the face of the pandemic, but now that companies are bringing employees back to the workplace, many are pushing back. While we can of course assist with your implementation of remote work technologies, there might be more reason to consider allowing for remote work. This doesn’t come from just us; it also comes from industry experts.
Have you heard the term “quiet quitting''?” It’s been going around lately, and it can be a problem if it isn’t addressed. Let’s examine what quiet quitting is, what it means for your business, and what you can do to solve it.
Most people will spend about one-third of their lives at work. Naturally, this large amount of time spent away from home can lead to a lot of stress. Emotions can overwhelm your employees and lead them to experience negative side effects that could impact their physical and mental health. Let’s examine some ways you can minimize the workday stressors that your employees may suffer from.
Worker burnout is more prevalent than ever, and it can lead employees to experience negative effects such as stress, exhaustion, depression, and frustration. Do you see any of these symptoms in your IT workers? Let’s take a closer look at how burnout is impacting the IT industry and your IT talent, as well as some ways you can address it.
We frequently discuss how the solutions we offer can make business processes and procedures more effective, but in doing so, we’ve frequently overlooked how the implementation of these solutions—especially in terms of your digital transformation—have impacted your human resources.
Collaboration is central to the success of any company’s sustained efforts, and technology plays an important role in making this happen. Let’s go over some collaboration best practices your business can implement, as well as how technology can help them be successful in these efforts.
For many companies, their first experiences with modern collaboration tools came about as a result of the unfortunate circumstances surrounding the COVID-19 pandemic. Some were forced to go entirely remote, while others completely halted operations for an indefinite period of time. While collaboration tools are designed to bring people together, it might come at a cost.
It doesn’t take a genius to understand the importance of IT maintenance and management, but it’s often easier said than done to make sure it happens properly. A new survey from Gartner suggests that this might get even more challenging, as IT employees are increasingly more likely to leave their place of work than other, non-IT employees.
Shadow IT is a considerable problem for businesses that rely on IT in their operations. Let’s take a quick look at what shadow IT really is and how it can impact your business. We’ll also discuss ways you can avoid it.
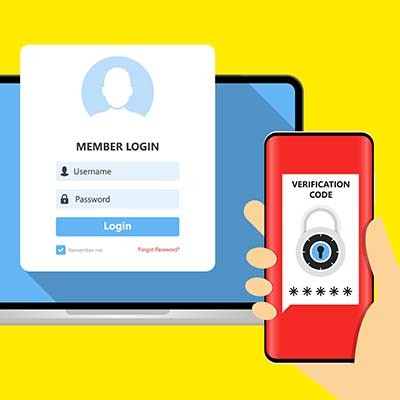
Have you ever heard of the concept of going passwordless? Considering how passwords have been central to data security and authentication for so long, you might be a little hesitant about the idea. However, data show that there are better options out there. Here are some of the better passwordless options your organization can implement.
Many companies have been using remote work for so long that there are growing concerns for how this will influence company culture moving forward. Let’s discuss how you can avoid having remote work directly impact your company culture so that your team can maintain a productive working relationship.